Practical Prepping Blog
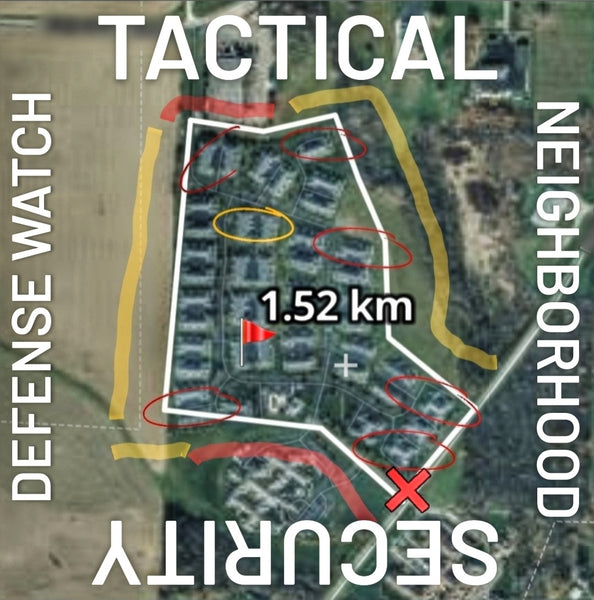
Tactical Neighborhood Watch - Security and Self-sufficiency following a Life Altering Event (SHTF)
In Case of Emergency or ICE Card - a quick guide.
Financial Prepping
Money and Prepping go hand in hand. Financial Prepping is a topic rarely discussed yet a challenge we all face daily.
Personal economic hardship, the preparation for a Life Altering Event (EMP, hurricane, civil unrest), and banking disruptions, represent the three reasons why finances should be considered as part of your overall preparedness plan.
Why plan now?
1. Unexpected vehicle repairs
2. Sudden medical expenses
3. Collapse of banking system
4. Civil Unrest and National State of Emergency
5. Job loss, death in family, birth of child
6. Government or Private seizure/freezing of funds
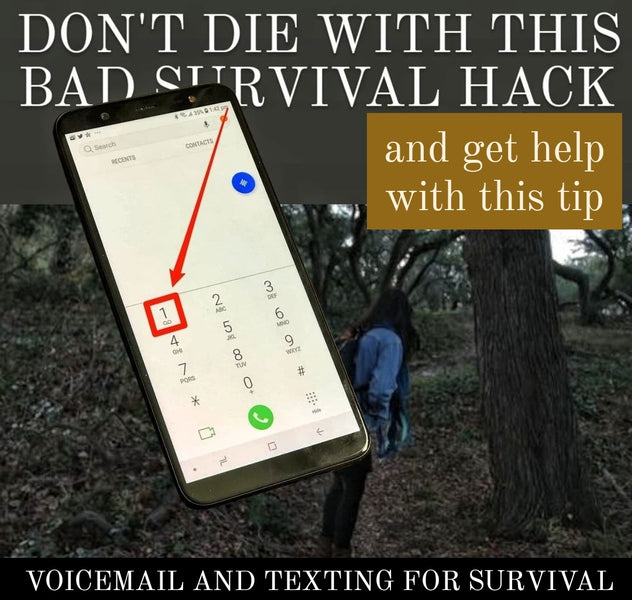
When not to use your voicemail in a worst case scenario and when to text 911
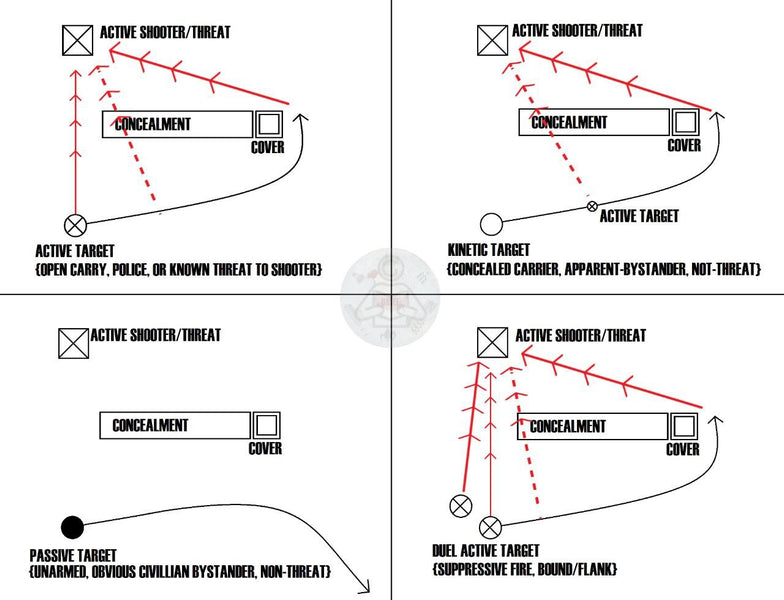
Active Shooter - React to and Break Contact
Responding to an active threat (shooter) will vary based upon the attention of the threat, your readiness, and your carry status (whether or not you have a firearm and if it's open or concealed carried). In the event a threat is actively engaging targets, you must take action. RUN, HIDE, FIGHT. There are endless scenarios and possible outcomes but in this "react to contact" drill we'll highlight the 4 best courses of action (COAs) for the below scenario. Keep in mind this is a generalized threat response and it can be applied to multiple scenarios.
For more lessons on an array of Tactics, Techniques, and Procedures; subscribe to the Grayman Briefing.
Divergent Urban Land Navigation and Water-Based Bugout Options
Situation Awareness for Home Security and Counter Surveillance
SCAME - Analysis of Information Warfare Source Enemy
Field Expedient Entry and Egress Keys - Access Tools
PMESII-PT Operational Environment Area Study
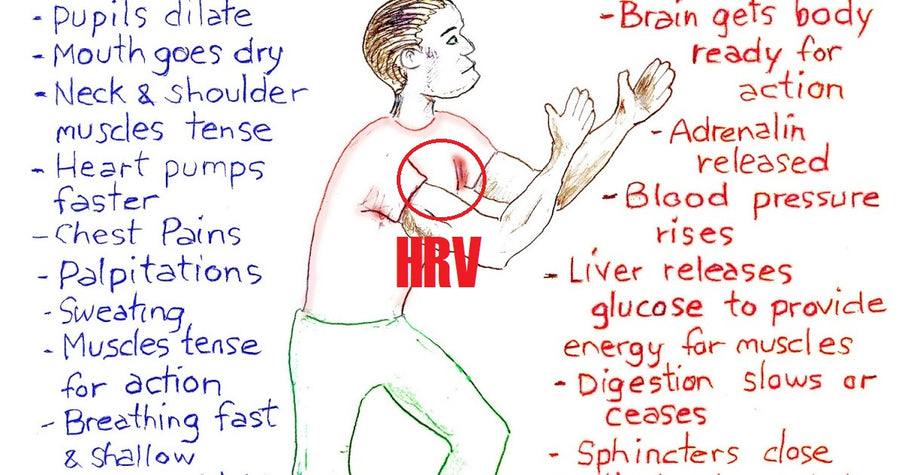
Heart Rate Variability and Relation to Threat Response via Situational Awareness
First let’s give a reminder on the Cooper’s Color Code. It all relat...